Your Access control list example images are ready in this website. Access control list example are a topic that is being searched for and liked by netizens now. You can Download the Access control list example files here. Find and Download all free vectors.
If you’re looking for access control list example images information connected with to the access control list example keyword, you have come to the right site. Our website always provides you with suggestions for refferencing the maximum quality video and picture content, please kindly search and locate more informative video content and graphics that match your interests.
Access Control List Example. User name and password and PIN numbers is another example of access control. Let me show you something useful when you are playing with access-lists. Amazon S3 access control lists ACLs enable you to manage access to buckets and objects. Issue the show access-list command in order to view the ACL entries.
 An Access Control List Acl Download Scientific Diagram From researchgate.net
An Access Control List Acl Download Scientific Diagram From researchgate.net
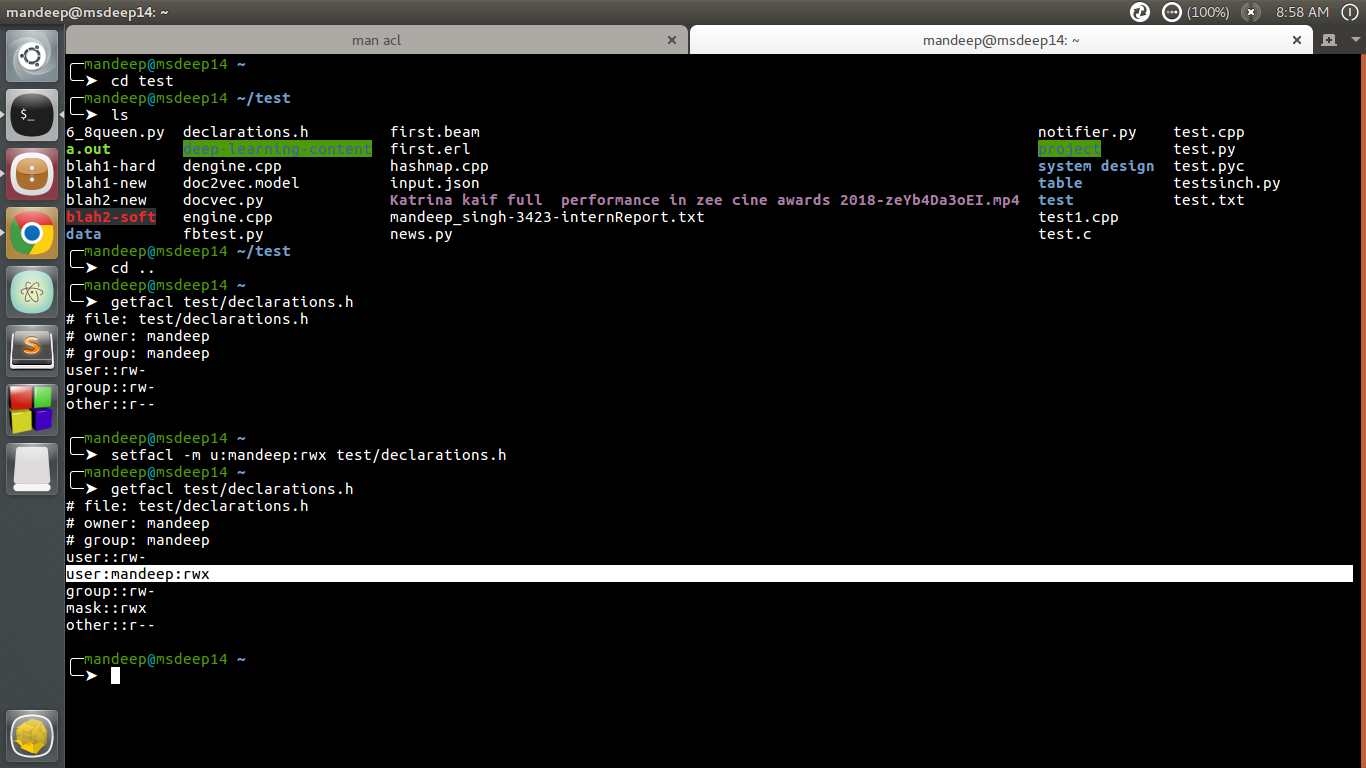
We can view the current ACL using the getfacl command. This type of situation is what Linux Access Control Lists ACLs were intended to resolve. A network protocol and associated function or ports. An ACL is the same as a Stateless Firewall which only restricts blocks or allows the packets that are flowing from source to destination. An ACL can contain multiple rules. To create an IP access list you must specify a number from the above pre-defined number ranges.
A DACL and a SACL.
Implement AI-driven security with SailPoints Access Modeling. They let us tack on access for other users or groups. Huawei switches and routers. Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic. Each ACE in an ACL identifies a trustee and specifies the access rights allowed denied or audited for that trustee. A rule is identified by a rule ID which can be set by a user or automatically generated based on the ACL step.
 Source: imperva.com
Source: imperva.com
An Access Control List ACL is a set of rules that classify packets to filter them. In computer security an access-control list ACL is a list of permissions associated with a system resource object. The security descriptor for a securable object can contain two types of ACLs. Access control is a security measure which is put in place to regulate the individuals that can view use or have access to a restricted environment. User name and password and PIN numbers is another example of access control.
 Source: geeksforgeeks.org
Source: geeksforgeeks.org
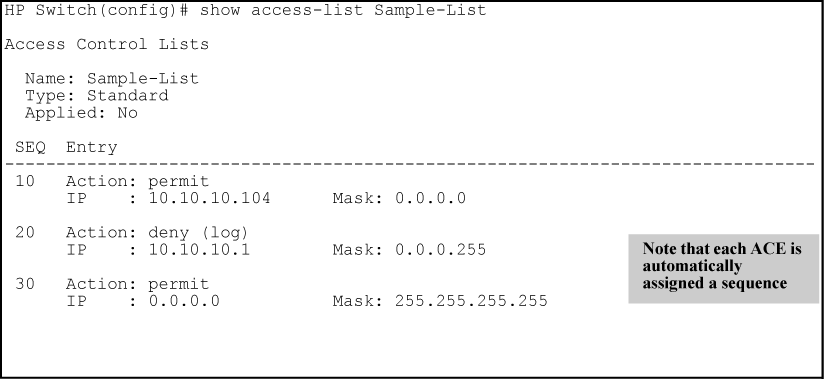
Add the entry for the access list 101 with the sequence number 5. An ACL specifies which users or system processes are granted access to objects as well as what operations are allowed on given objects. Let me show you something useful when you are playing with access-lists. The sequence numbers such as 10 20 and 30 also appear here. An access control list ACL contains rules that grant or deny access to certain digital environments.
 Source: in.pinterest.com
Source: in.pinterest.com
To learn about how to incorporate Azure RBAC together with ACLs and how system evaluates them to make authorization decisions see Access control model in Azure Data Lake Storage Gen2. Issue the show access-list command in order to view the ACL entries. Ad For a highly targeted approach to data security grant access based on attributes. A network protocol and associated function or ports. An Access Control List ACL is a set of rules that classify packets to filter them.
 Source: pinterest.com
Source: pinterest.com
Ad For a highly targeted approach to data security grant access based on attributes. There are two types of ACLs. R2show access-lists Standard IP access list 1 10 permit 192168120 wildcard bits 000255 27 matches As you can see the access-list shows the number of matches per statement. We can view the current ACL using the getfacl command. A statement of permission or denial for that entry.
 Source: online-tech-tips.com
Source: online-tech-tips.com
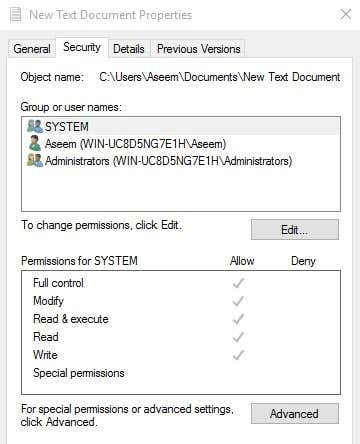
Access control is a security measure which is put in place to regulate the individuals that can view use or have access to a restricted environment. You can associate a security principal with an access level for files and. Amazon S3 access control lists ACLs enable you to manage access to buckets and objects. Biometric to access the data centres and computer rooms. A rule is identified by a rule ID which can be set by a user or automatically generated based on the ACL step.
 Source: slideplayer.com
Source: slideplayer.com
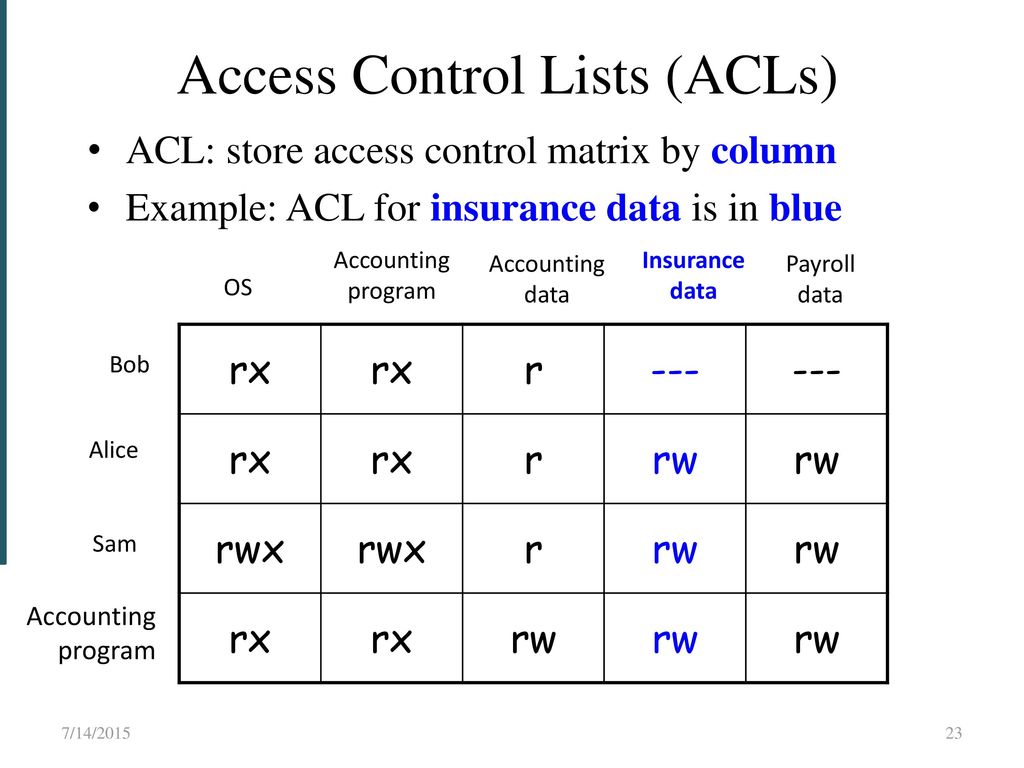
Each bucket and object has an ACL attached to it as a subresource. The security descriptor for a securable object can contain two types of ACLs. A rule is identified by a rule ID which can be set by a user or automatically generated based on the ACL step. An ACL specifies which users or system processes are granted access to objects as well as what operations are allowed on given objects. Each ACE in an ACL identifies a trustee and specifies the access rights allowed denied or audited for that trustee.
 Source: slideplayer.com
Source: slideplayer.com
Networking ACLs filter access to. User name and password and PIN numbers is another example of access control. Issue the show access-list command in order to view the ACL entries. Access Control List example Huawei Technology. Each ACE in an ACL identifies a trustee and specifies the access rights allowed denied or audited for that trustee.
 Source: pinterest.com
Source: pinterest.com
Let me show you something useful when you are playing with access-lists. Access control lists ACLs Service ACLs route maps and prefix lists are all processed in order beginning with the first rule and proceeding until a match is encountered. Standard access-list for Telnet example As you know you cannot specify particular IP traffic to be denied in standard access-list but telnet connection can be permitted or denied using standard access-list by applying access-list on line vty lines. Let me show you something useful when you are playing with access-lists. An access control list ACL is a list of rules that control the inbound flow of packets into Ethernet interfaces subinterfaces and port channel interfaces or the switch.
 Source: researchgate.net
Source: researchgate.net
ACLs work on a set of rules that define how to forward or block a packet at the routers interface. This article describes access control lists in Data Lake Storage Gen2. Access Control Lists Access control lists ACLs are used by many different features. To create an IP access list you must specify a number from the above pre-defined number ranges. Networking ACLs filter access to.
 Source: techhub.hpe.com
Source: techhub.hpe.com
The sequence numbers such as 10 20 and 30 also appear here. Access Control List example Huawei An Access Control List ACL is a set of rules that classify packets to filter them. For example to create a standard IP access list you can choose any number between 1-99 and 1300-1999. Examples include IP IPX ICMP TCP UDP NETBIOS and many others. To create an IP access list you must specify a number from the above pre-defined number ranges.
 Source: ccie-or-null.net
Source: ccie-or-null.net
A network protocol and associated function or ports. Each entry in a typical ACL specifies a subject and an operation. Some Example of Access Control from my own experience Access cards for access sensitive areas. You can associate a security principal with an access level for files and. This happens by either allowing packets or blocking packets from an interface on a router switch firewall etc.
 Source: theitbros.com
Source: theitbros.com
A network protocol and associated function or ports. An ACL specifies which users or system processes are granted access to objects as well as what operations are allowed on given objects. An ACL can contain multiple rules. We can view the current ACL using the getfacl command. Let me show you something useful when you are playing with access-lists.
 Source: nl.pinterest.com
Source: nl.pinterest.com
Various access control examples can be found in the security systems in our doors key locks fences biometric systems motion detectors badge system and so forth. They let us tack on access for other users or groups. Add the entry for the access list 101 with the sequence number 5. An ACL specifies which users or system processes are granted access to objects as well as what operations are allowed on given objects. The sequence numbers such as 10 20 and 30 also appear here.
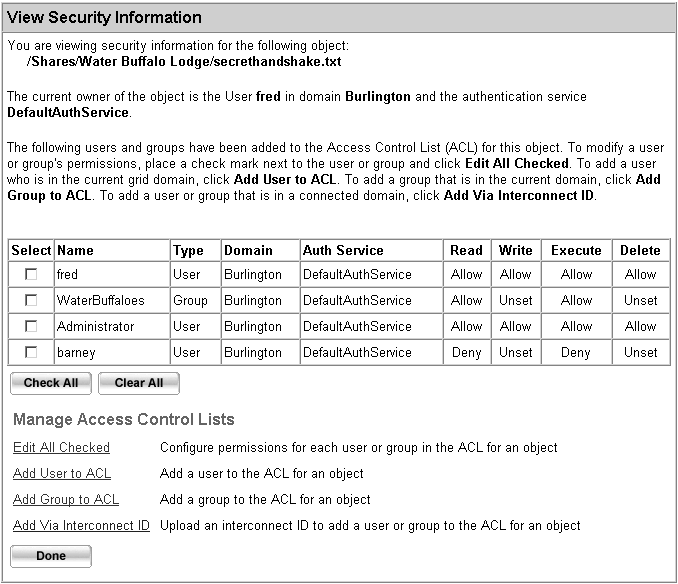 Source: infocenter.sybase.com
Source: infocenter.sybase.com
Understanding Access Control List with some Examples To understand the access control we will look at some examples based on the Unix system. A statement of permission or denial for that entry. Examples include IP IPX ICMP TCP UDP NETBIOS and many others. Standard access-list for Telnet example As you know you cannot specify particular IP traffic to be denied in standard access-list but telnet connection can be permitted or denied using standard access-list by applying access-list on line vty lines. Various access control examples can be found in the security systems in our doors key locks fences biometric systems motion detectors badge system and so forth.
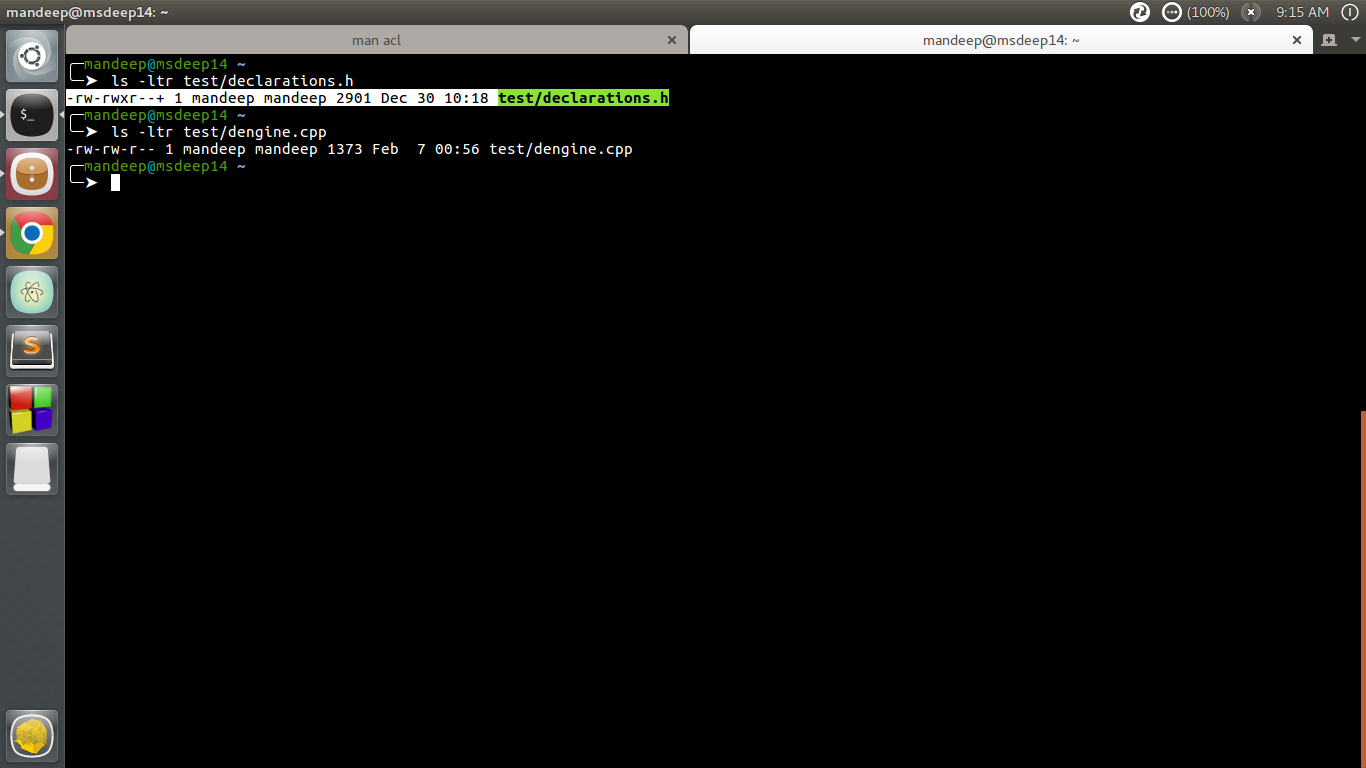 Source: geeksforgeeks.org
Source: geeksforgeeks.org
Huawei switches and routers. A statement of permission or denial for that entry. For example to create a standard IP access list you can choose any number between 1-99 and 1300-1999. To learn about how to incorporate Azure RBAC together with ACLs and how system evaluates them to make authorization decisions see Access control model in Azure Data Lake Storage Gen2. A rule is identified by a rule ID which can be set by a user or automatically generated based on the ACL step.
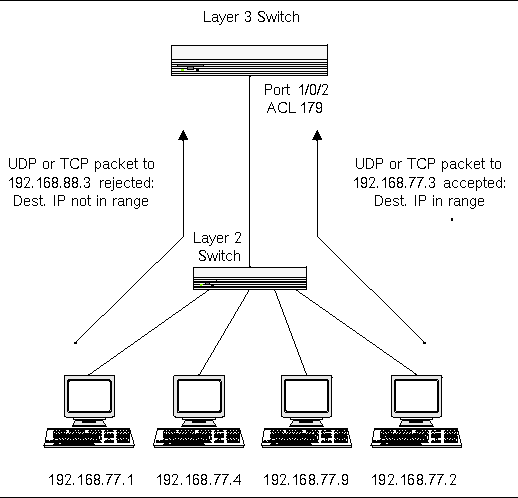 Source: docs.oracle.com
Source: docs.oracle.com
Access control list name depending on the router it could be numeric or combination of letters and numbers A sequence number or term name for each entry. To learn about how to incorporate Azure RBAC together with ACLs and how system evaluates them to make authorization decisions see Access control model in Azure Data Lake Storage Gen2. A DACL and a SACL. Similarly to create an extended IP access list you can select any number between 100-199 and 2000-2699. It defines which AWS accounts or groups are granted access and the type of access.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Each bucket and object has an ACL attached to it as a subresource. An ACL can contain multiple rules. An ACL specifies which users or system processes are granted access to objects as well as what operations are allowed on given objects. To learn about how to incorporate Azure RBAC together with ACLs and how system evaluates them to make authorization decisions see Access control model in Azure Data Lake Storage Gen2. An Access Control List ACL is a list of rules that control and filter traffic based on source and destination IP addresses or Port numbers.
 Source: pinterest.com
Source: pinterest.com
Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic. Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic. An ACL is the same as a Stateless Firewall which only restricts blocks or allows the packets that are flowing from source to destination. Access Control Lists ACLs are a collection of permit and deny conditions called rules that provide security by blocking unauthorized users and allowing authorized users to access specific resources. An Access Control List ACL is a set of rules that classify packets to filter them.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title access control list example by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






